Our rant on why you should change your bloody password!
Hi Friends,
I’m not going to be polite. I’m not going to be gentle. I’m going to stop you from being the next muppet.
Change your passwords today.
Ending up on the wrong side of a password theft has happened to too many of my friends recently. From being locked out of a computer to having your aunt sent pictures on Facebook that she’d rather not have seen, the sob stories don’t read well. And you should do these three things today to make sure you’re not next.

Don’t be these two.
Number One
Your passwords should be random and generated by something other than you. Can’t remember all those weird characters? Cool. Neither can I. So:
- Get a password manager (I don’t care what, but Keychain on Apple or LastPass or Google). These will keep your passwords safe and encrypted, serve them back up to you if you need them to log into something, and may even suggest passwords for you. If they don’t suggest passwords, see below.
- Once you have this set up, make sure that your password for this service is really strong. Make it with a series of words that you’re unlikely to forget. This is the one password that you can’t afford to forget. It’s also the keys to your fiefdom, so if you choose password123 you’re setting yourself for a pwning.
Your new password manager will do most of the hard work from now on:
- Remembering the passwords for you
- Helping you fill them in on your phone and laptop
- Keeping them safe

Keep ’em locked up
Number Two
For crying out loud, stop using that {car} + {year} or {street} + {age} formula for your passwords. Stop using the road you grew up on. Stop using anything you can read. Stop it now!
For your most important accounts change your passwords immediately. Start with these:
- iCloud or Microsoft
- Gmail (or your other email)
- TradeMe
- Anywhere you’ve got saved payment options
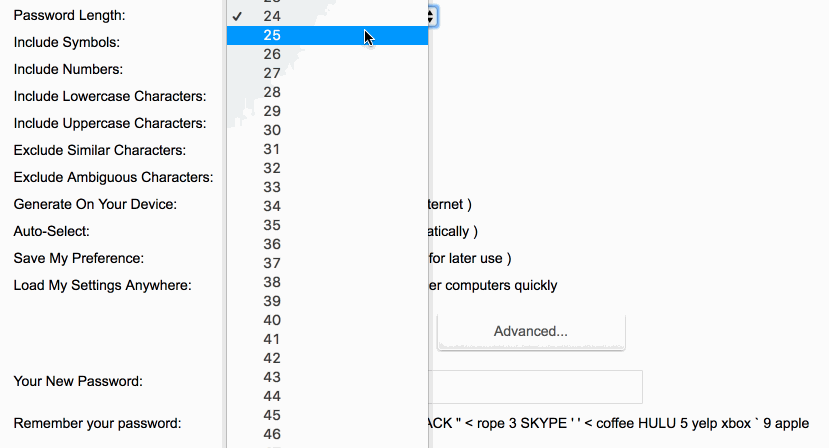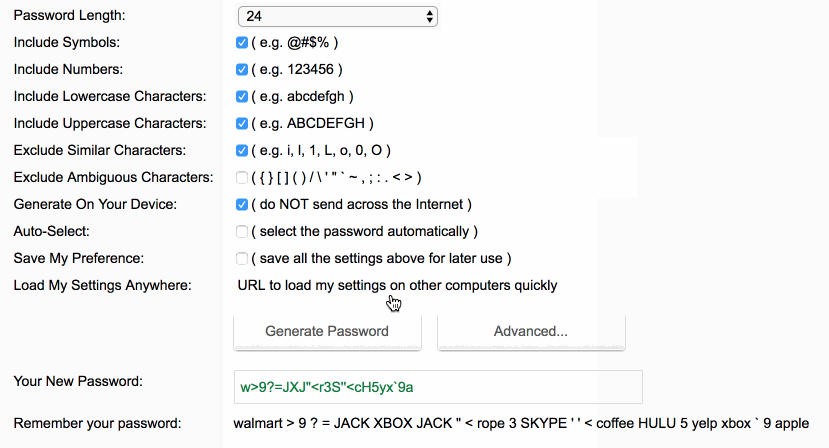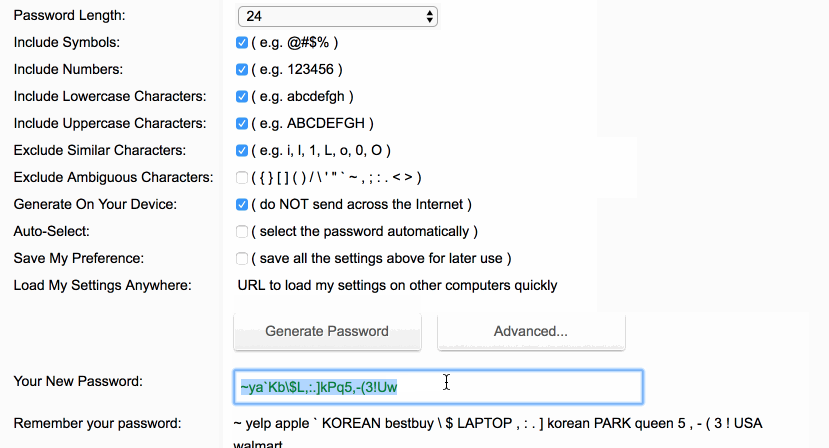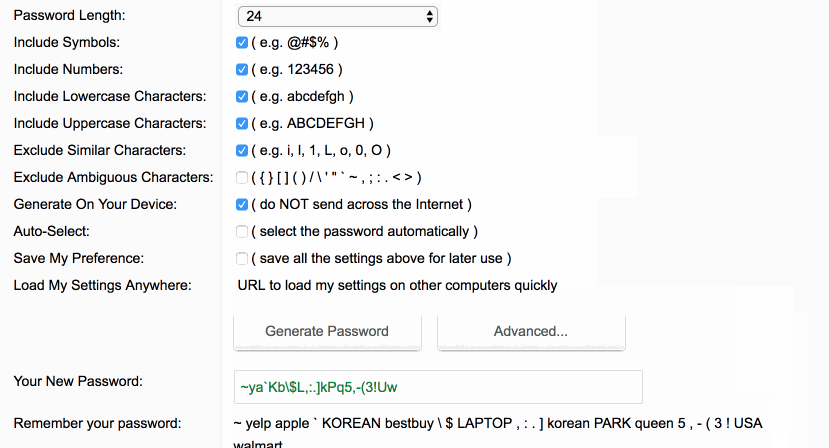
When you select a new password, make sure you have your new Password Manager suggest the password. If it won’t suggest a password, use this tool. It’ll look like this:
w>9?=JXJ”<r3S’’<cH5yx`9a
But who cares; nobody is going to brute force that in a hurry. You don’t need to remember it so why not make it hard! The key here is to make sure that each password is different. Never use the same password again. Ever.
Number Three
Go and turn on Multi-Factor Authentication for the above accounts. Make sure you do it for your email! Don’t know how? The most simple incarnation of this is the humble text message. When you try to log in company x sends you an sms, you enter the code in the text, and bingo. (Also treat this wee code like it’s your password. Never do anything with it except typing it into the website you’re logging into.) Apple can also have you authenticate from another device, whilst Google will do something similar with their app on iOS and Android. Whatever it is, make sure there is something physical that is required to get into your account. A phone that receives a text for example.
A Closing Story
Three years ago I was in Italy. It was lovely. Whilst winding down over a beer from a day driving between the beaches of the Amalfi Coast I received the dreaded Call Me ASAP text message. My 2IC was incredibly competent and had pretty much everything handled. What could possibly have gone wrong?
Our policy that Multi-Factor Auth had to be turned on had slipped through the cracks. A password was compromised through a third party website; the email and password combination was out in the wild. (A simple nslookup will show you who hosts the mailbox for an email address).The email account was used to email our bank, convincing some poor girl there that James is away, and he’s left me in charge. She obediently sent, by FedEx Overnight, three cashiers checks (this was in the US of course) totalling USD50,000.
Boom! Fifty Grand!

It’s scarily simple to work out what many people’s passwords are, especially if they reuse them. And once you can access their email account you can pretty much reset all of their passwords.
Don’t be a muppet. Have you:
- Set up a password manager; and,
- Changed your important passwords; and,
- Turned on MFA?
Do these and you’re about 90% of the way to being much safer online.
Notes and extras
- The debates over whether to use a browser password manager will go on and on, and they’re not the best that money (or no money) can buy, but they’re the most that most people will tolerate. The convenience vs security balance is in their favour.
- Have your computer lock itself after a sensible timeout of perhaps a minute, because physical access always trumps everything else.
- Always access sites using HTTPS. Look for a green EV lock in the address bar for confidence that you’re on the correct and a trustworthy site.
- Don’t write down your passwords in a book and carry it around, or worse, lose it.
- There are other ways to make sure you don’t get pwned online, this is merely a start. But aim to continuously improve, be better than most, and there will be easier targets for the less desirable.
- If you want to see if you’ve been pwned (i.e. some of your passwords are in the wild), look at Have I Been Pwned.
- [Update - July 2019] Check out this thorough blog post from the team at PixelPrivacy if you really want to get into the weeds of passwords.
Share this
You May Also Like
These Related Stories

Why should smaller businesses switch to a cloud phone system?
